Apache HertzBeat (incubating) is an easy-to-use, open source, real-time monitoring system with agentless, high performance cluster, prometheus-compatible, offers powerful custom monitoring and status page building capabilities.
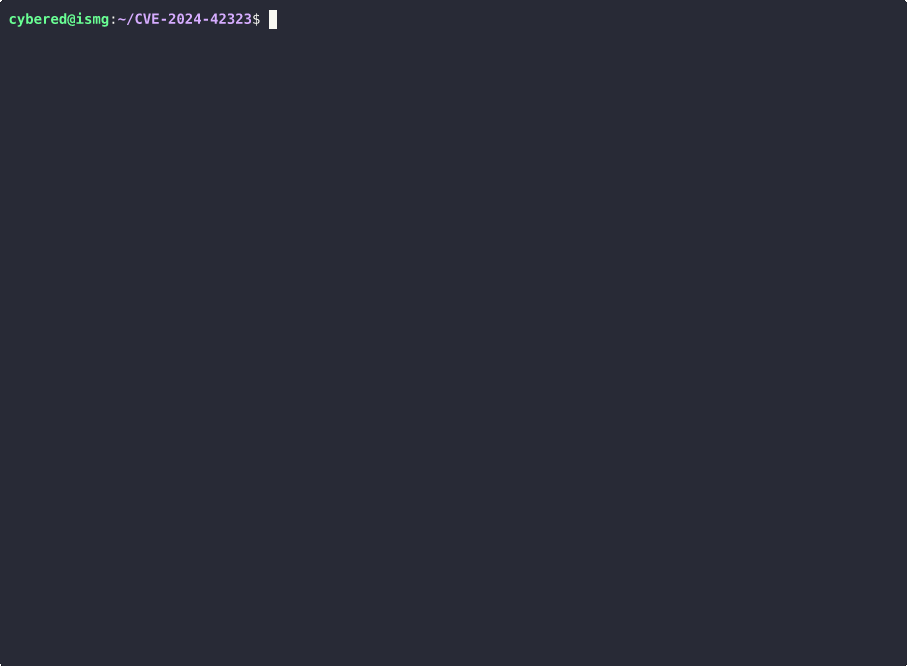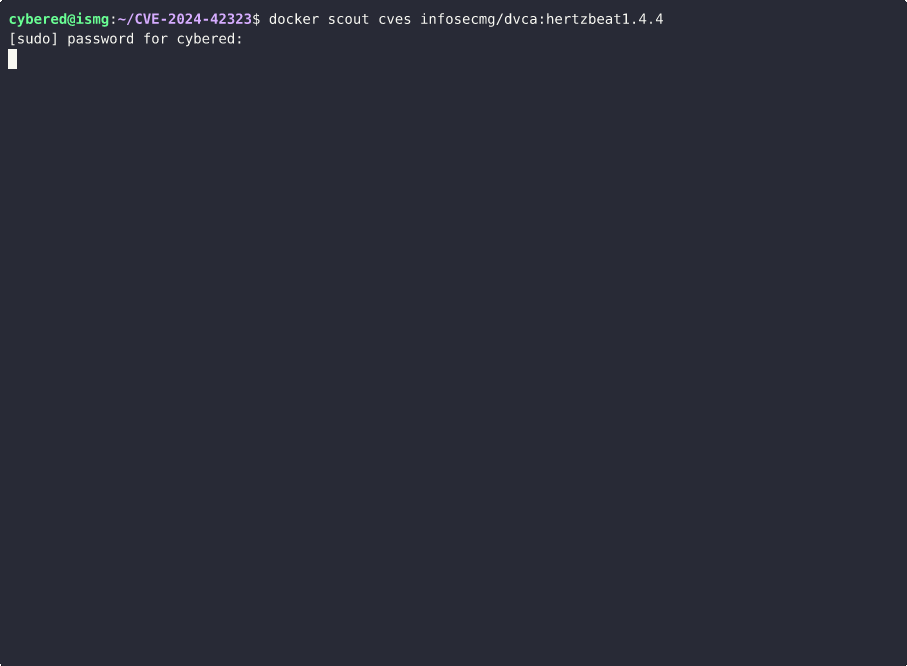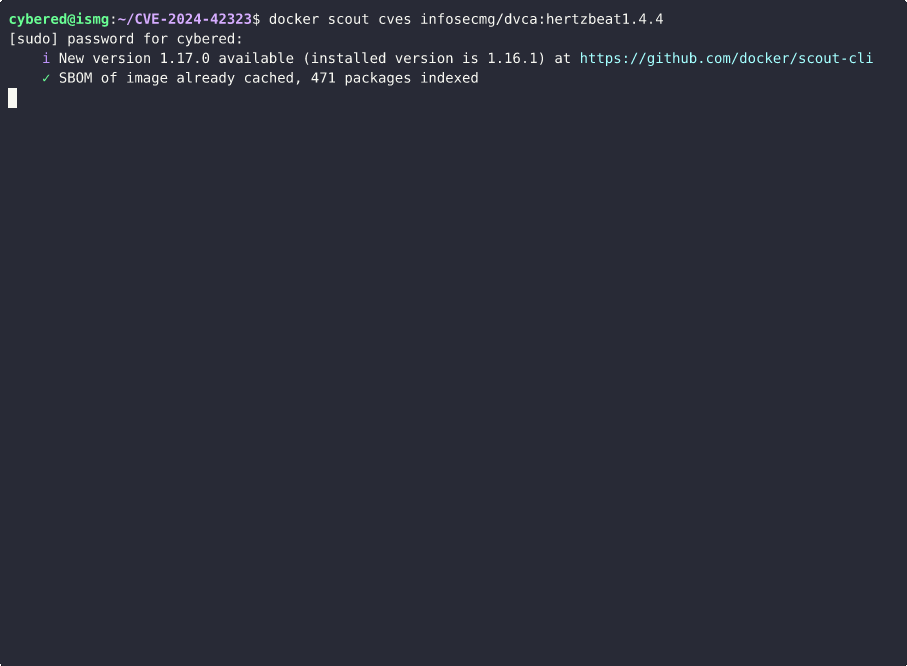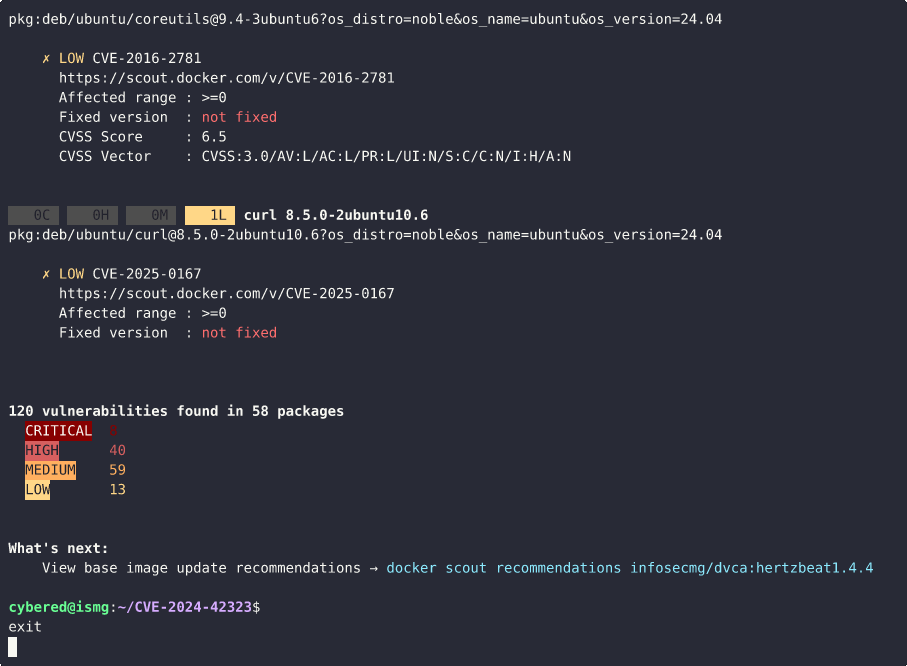
CVE-2024-42323 is a SnakeYaml deserialization vulnerability in Apache HertzBeat (incubating) that can lead to remote code execution (RCE). This vulnerability can only be exploited by an authorized user.
Objectives:
- Verify and deploy a vulnerable application as a Docker Container;
- Exploit using custom payloads;
- Detect threats using runtime security tools like Falco;
- Enforce best practices and secure container environments against breaches.
Ideal for Security Professionals, DevOps Teams, and Penetration Testers
Here is the course outline:
In-House Labs |
Completion
The following certificates are awarded when the course is completed:
 |
CPE Credit Certificate |



